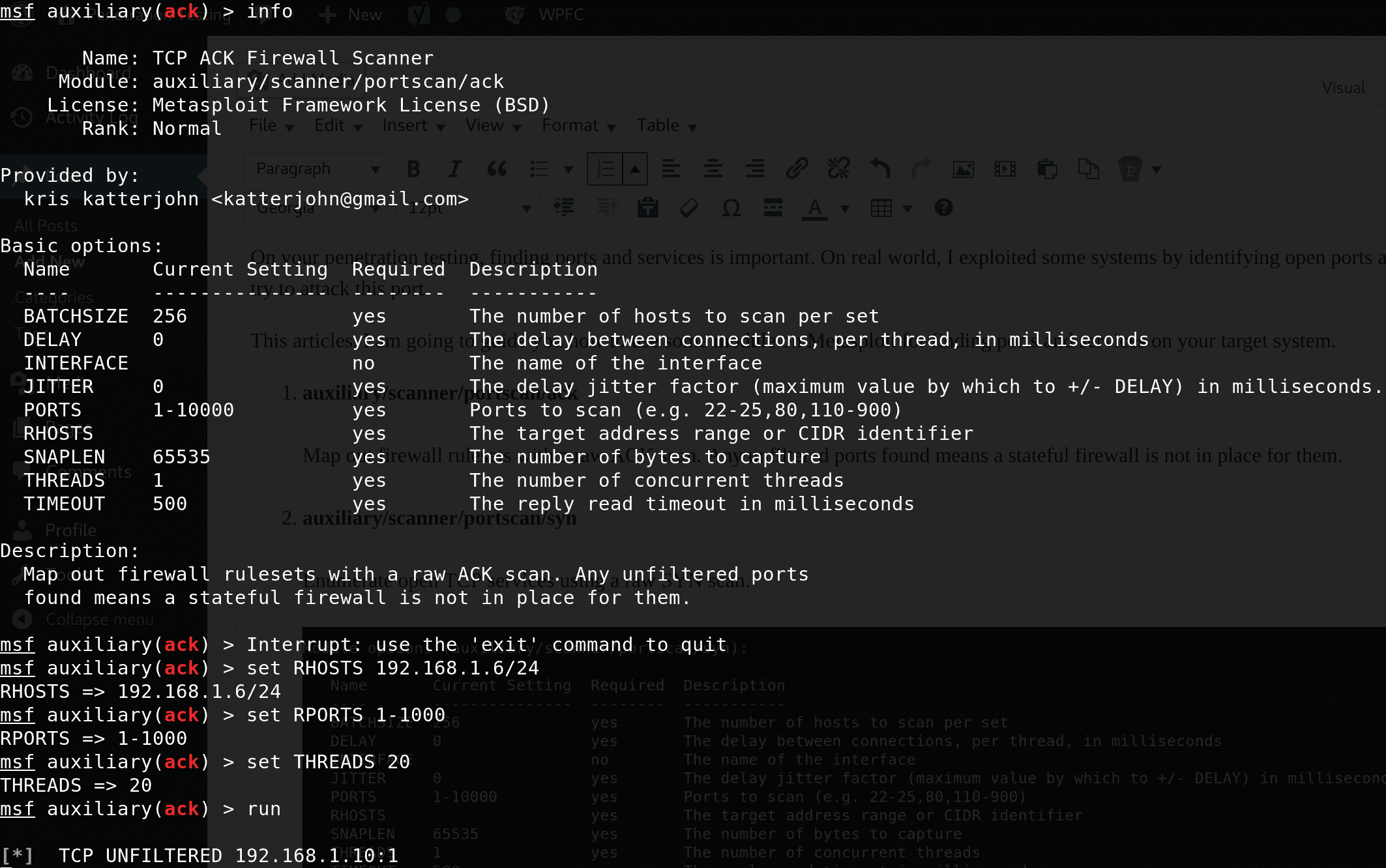
The port scan techniques are different for TCP and UDP ports, that is why we have dedicated tools for each one. Perform website penetration testing, network security assessments and advanced reconnaissance using our platform. Listelediğimiz auxiliary modüllerinden kontrol ettik örnek olarak port taraması gerçekleştireceğiz. MSF konsolumuzda aktif edelim. Port Taraması gerçekleştirelim.
Hedefimizi, taratmak istediğimiz. This tool is a personal project of Javier Yanez, available to use in free to scan the ports against IPVor IPVaddress. Scan the individual or range ports listening on server IP. Tis useful if you want to scan the targeted ports. Profiles kısmı altında hazır tarama profilleri yer alıyor.
Owasp_Topbölümünde ise owaspta bulunan en tehlikeli açığın taramasını otomatik olarak seçebilirsiniz. Bir çok açık tarama çeşidi mevcut fakat bu taramaları daraltırsanız sizin için zaman kaybı yaşanmayacaktır. Leading source of security tools, hacking tools, cybersecurity and network security. Learn about new tools and updates in one place.
The port scanner that we will use is the syn scanner and we can see the configuration settings in the image below:. Mass Scan - TCP port scanner ,. Sn1per - Automated Pentest Recon Scanner. Spiderfoot - Multi-source OSINT automation tool with a Web UI and report visualizations. Dear PenTest Readers, In the current issue we would like to take a closer look at security of the Kubernetes system. His vulnerability scanner found that there was a system inside the network established to track the hacker’s activities.
A honeypot has the same functionalities as the main server. Pentest işlemlerinde test ortamının elinizin altında olması anlık müdahale durumunun bulunması,etki tepkiyi hızlı ölçebilme,yapılan pentest işlemlerinde gerek savunma gerek saldırı vektörlerinin herhangi bir risk taşımadan gerçekleştirebilmesi adına Wamp server vb. An open port scanner is a tool which is used to check the external IP address and identify open ports on the connection.
It is used to detect whether the port forwarding is setup accurately or the server applications are being blocked by a firewall. Open source network scanner that enables researchers to easily perform Internet-wide network studies. Utility for using websites to perform port scans on your behalf so as not to reveal your own IP.
DNSDumpster - Online DNS recon and search service. To make sure all unessential ports are close a port scanner is an invaluable tool and we’re glad to present this list of the best port scanning software tools. A good recon can make a difference between a successful and failed result.
One of the methods used during active reconnaissance is port scanning. Reconnaissance can be categorized into two: active and passive. A powerful tool for managing networks and troubleshoot network problems!
Features Network Interface – Information, Configure IP-Scanner Port-Scanner Ping. At first it might seem that there are a ton of ‘similar’ tools. Herkese Öncelikle İyi Haftasonları Bu Konumda Bir Tcp-İp Protokolü Olan Ftp Protokolüne Pentest İşlemi Gerçekleştireceğiz İlk Olarak Ftp ve Pentest Nedir. DNS Çözümlemesi yapma anlamına gelir.
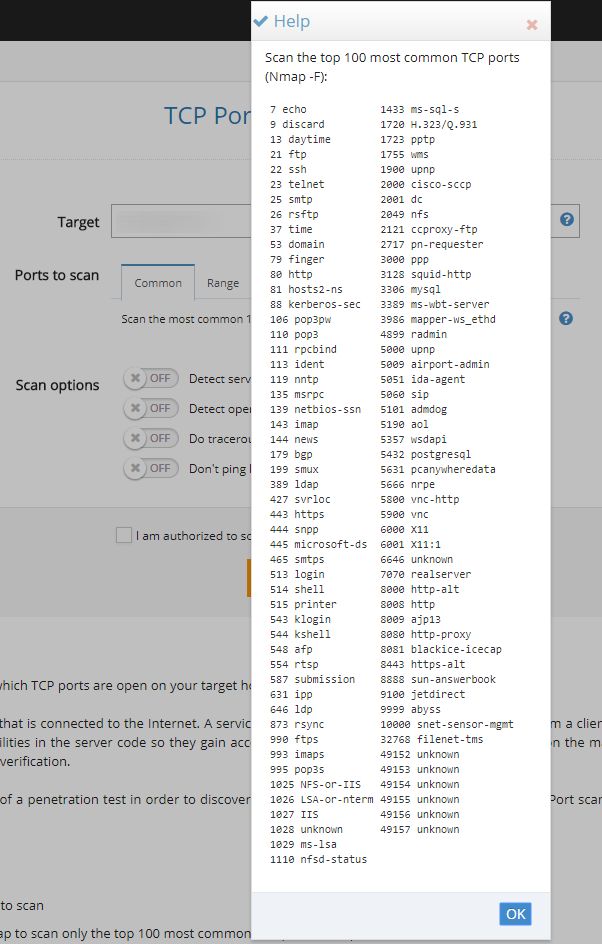
Ekrana gösterilecek detayları arttırır. SANS Penetration Testing. To create a PowerShell port scanner in one line we need to combine three distinct components. Creating a range of objects, looping through each object, and outputting information for each to the screen.
Das Programm bietet eine anwenderfreundliche Bedienoberfläche sowie zahlreiche Funktionen. Infrastructure PenTest Series : Part - Vulnerability Analysis¶. So, by using intelligence gathering we have completed the normal scanning and banner grabbing.
Now, it’s time for some metasploit-fu and nmap-fu. Metasploit for website pentest using wmap. Wmap is a web application scanner that runs within metasploit.
We can use wmap to get an outline of the application we are probing. The term security assessment refers to all activity engaged in for the purposes of determining the efficacy or existence of security controls amongst your AWS assets, e. Girişimizi yaptıktan sonra Policies kısmından Add’i tıklayarak pentest yapmak üzere bir tarama kuralı oluşturuyoruz. Eğer Nessus scanner’ı bir sunucu üzerine kurup client ile tarama yapacak isek Visibility kısmını Shared olarak seçiyoruz.

Aksi durumda Private kalmasında bir sakınca yoktur.
Hiç yorum yok:
Yorum Gönder
Not: Yalnızca bu blogun üyesi yorum gönderebilir.