Powered by ThreatCloud Intelligence. Did you find it helpful? The map is more visual than the one from Norse, but still has the same. ThreatCoud IntelliStore makes it easy to access relevant and up-to-date cyber threat intelligence feeds—and turn it into actionable security in your network. Malware is constantly evolving, making threat intelligence an essential tool for every organization.
With ThreatCloud IntelliStore we make it easy to access. Latest Research by our Team. Real-Time Cyber Threat Map : Use our interactive Cyber Threat Map which shows in real time the geolocation of cybercrime servers that are actively engaged in criminal activity such as credit card theft, credential theft or malware distribution. Check Point Software Blog. Dynamic Threat Defense - LookingGlass Dynamic Threat Defense (DTD) is a LookingGlass cyber security solution that utilizes the Cyveillance Malicious CData Feed to automatically mitigate threats via LookingGlass DNS Defender.
DTD allows your organization to be automatically protected from threats such as embedded malware, viruses and trojans. Linc is an SaaS video conferencing solution used for online meetings, webinars, and e-learning sessions. It’s not the most advanced in our list, but it does a good job of showing live stats for today’s and yesterday’s attacks. Find more data about threatmap. Filter by a category, type or risk level and search for a keyword or malware.
Why it’s a Smart Idea to Use Threat Intelligence. When It Comes to Security, Do You Have ‘Evidence-Based Knowledge’? Recently, I participated in an interesting Twitter chat. About Threatbutt Internet Hacking Attack Attribution Map By leveraging our patented Clown Strike technology we are able to harness the raw power of private, hybri public and cumulus cloud system to bring Viking grade threat intelligence to any enterprise.
And we made it into a map. Is your network security keeping up with the latest threats? FireEye Cyber Threat Map. View the latest Fortinet Threat Map and sign-up for a free threat assessment. Real-time global botnet threat map.
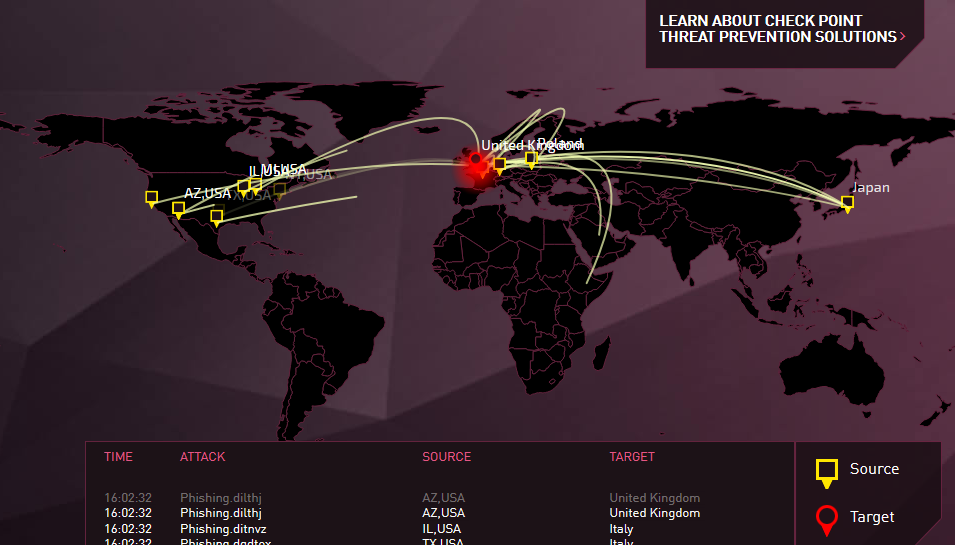
View the IP address locations of servers used to control computers infected with malware. Live botnet threats worldwide The IP address locations of servers used to control computers infected with malware. More and more security companies use a webpage to show their monitored global security events such as the Live Status of Cyber Attacks being launched from where and who is the target of that attack. It is become interesting by watching those websites. Actually those are not games but actually happening globally.
Kaspersky CYBERTHREAT REAL-TIME MAP 2. ThreatCloud World Cyber Threat Map, which visualizes how and where cyberattacks are taking place worldwide, in real time. We collected one metadata history record for Threatmap. Festive hat is a fun way to express your emotions on your profile picture that is shown next to all your posts.
It costs a small amount of Gold Points and your contribution will help to build a better online community. The hat will be automatically removed after month, or you can also remove it in your profile. Only connect to safe networks. This real-time map shows unsafe networks around the world. Some indicate malicious attacks, while others are insecure and should not be used for business or sensitive communications.
Cyber attack maps provide some awesome details on current cyber attacks in real time. Here is a quick list of cyber attack threat maps. Title : Real Time Cyber Threat Maps.

Summary : Video featuring some of the threat maps on the web. The Digital Attack Map, Arbor’s live DDoS and cyber-attack map, provides a live visualization of DDoS attacks throughout the worl offering a stunning visualization of how pervasive. Cyber threat analysis is a process in which the knowledge of internal and external information vulnerabilities pertinent to a particular organization is matched against real-world cyber attacks. With respect to cyber security, this threat -oriented approach to combating cyber attacks represents a smooth transition from a state of reactive.
It really depends on the efficiency of the thing.
Hiç yorum yok:
Yorum Gönder
Not: Yalnızca bu blogun üyesi yorum gönderebilir.