Digital Attack Map - DDoS attacks around the globe. Copy this code into your dismiss. Shows both large and unusual attacks. See recent global cyber attacks on the FireEye Cyber Threat Map.
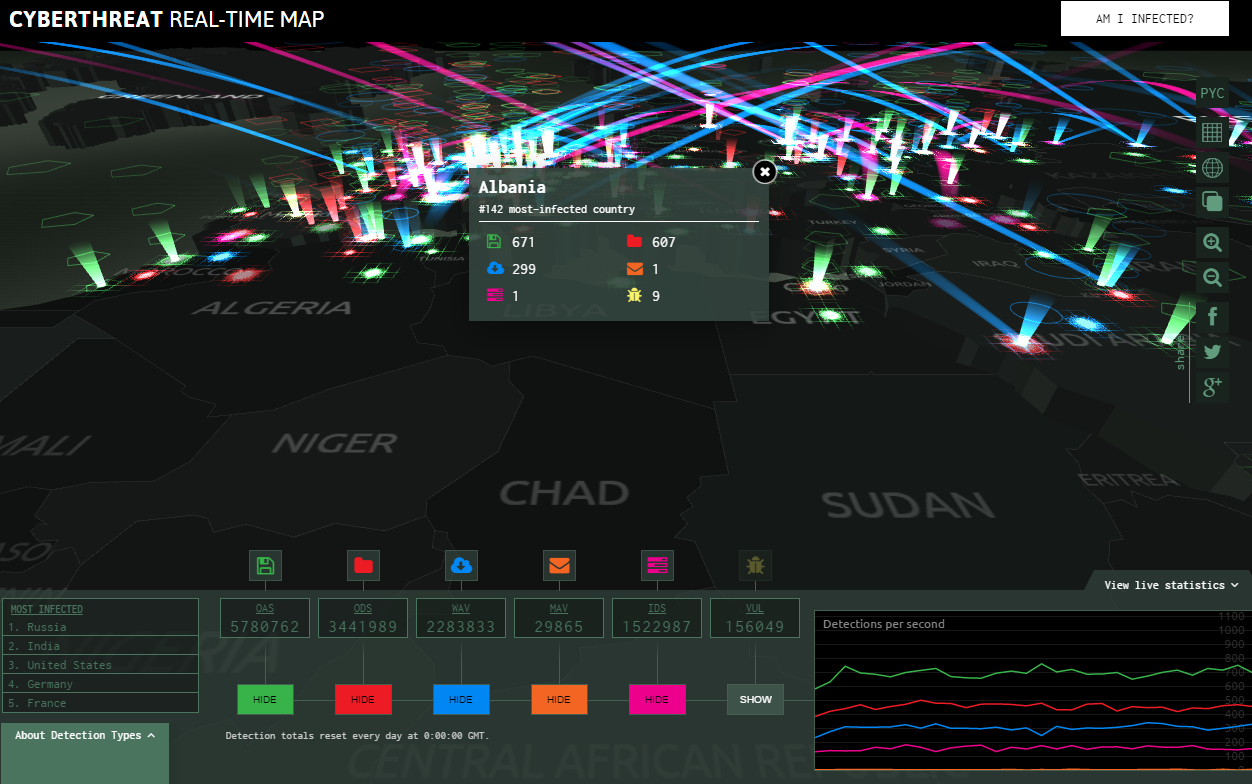
It’s interesting to watch who is initiating cyber-attack whom globally live. Thousands of website gets hacked every day due to vulnerable files, plugins, misconfiguration on the servers. If your website owner or administrator, you can perform security scan against your website to check vulnerabilities and malware. This is why all robust anti-virus software has long been using the Internet to study newly compromised files and the freshest threats as soon as they pop up. We plot this data on a map of the world in real time so you.
Once you load the map, it detects your current location and show you stats for your country, including historical top local infections for the last week. Kaspersky Cyber Malware and DDoS Real-Time Map. The cyber attack map from Arbor Networks is a hybrid map that was. It looks incredibly sleek. Click statistics to easily find lots of details on where the data is coming from and scan the attack rankings for the day.

Distributed Network Attacks are often referred to as Distributed Denial of Service (DDoS) attacks. This type of attack takes advantage of the specific capacity limits that apply to any network resources – such as the infrastructure that enables a company’s website. Various companies who are touting their cyber security offering like to throw these up behind them during photo ops. They are impressive, but more importantly they show us the unseen cyber world and the fact we are under attack. Beneath the 3-D eye candy and kaleidoscopic map is anonymized data.
Products to Protect You. Our innovative products help to give you the Power to Protect what matters most to you. Discover more about our award-winning security. Look at Cyberwar With Your Own Eyes: An Interactive Map of Online Threats. Y ou have an opportunity to see the scale and magnitude of the problem with your own eyes thanks to our map depicting malware epidemics in real time.
It is a kind of attack when an attacker is using special software to guess the password for your account. The shorter and simpler password you use, the sooner a hacker will guess it. Procrastinating on Software Updates. Stay protected and download your free malware protection tools today.
Threat Center is McAfee’s cyberthreat information hub. From here, you can learn about top cybersecurity threats in our continuously curated Threat Landscape Dashboar search our McAfee GTI database of known security threats, read in-depth threat research reports that detail significant attacks and how to protect against them, access a variety of free security tools. Deteque is another botnet attack map that provides a ton of useful. Threatbutt Internet Hacking Attack Attribution Map. Ransomware refers to malicious software that blocks access to a computer system until a ransom is paid.
How to detect a hacker attack. Due to this, detecting hacker attacks is not an easy task, especially for an inexperienced user. This article gives a few basic guidelines to help you figure out either if.
But this time the perpetrators were hiding. A unified security solution for a new era of digital transformation. This map shows just 20attacks for today. And below (click image for real-time updates) is the WCRYPT exploit specific events.
Geçen ayın en önemli olayı devasa DDoS saldırısıydı. Bu saldırı ile 80’den fazla büyük internet sitesi ve online hizme sağlayıcısına erişilemedi. Bu saldırının en önemli noktası, internete bağlanabilen her cihazdan ordu kurup bu ordu ile saldırılması oldu.
Biz buna Nesnelerin İnterneti (Internet of Things – IoT) diyoruz. In the event of a successful attack , the target software or hardware stops responding to legitimate requests. Interactive cyber- attack map by HTTPCS : Real time Website attacks, Vulnerable Websites, Malicious Websites, Malware providers.
Search a specific domain or a word. Take advantage of our free discovery offer to be alerted of cyber attacks and public security flaws related to your domain name.
Hiç yorum yok:
Yorum Gönder
Not: Yalnızca bu blogun üyesi yorum gönderebilir.