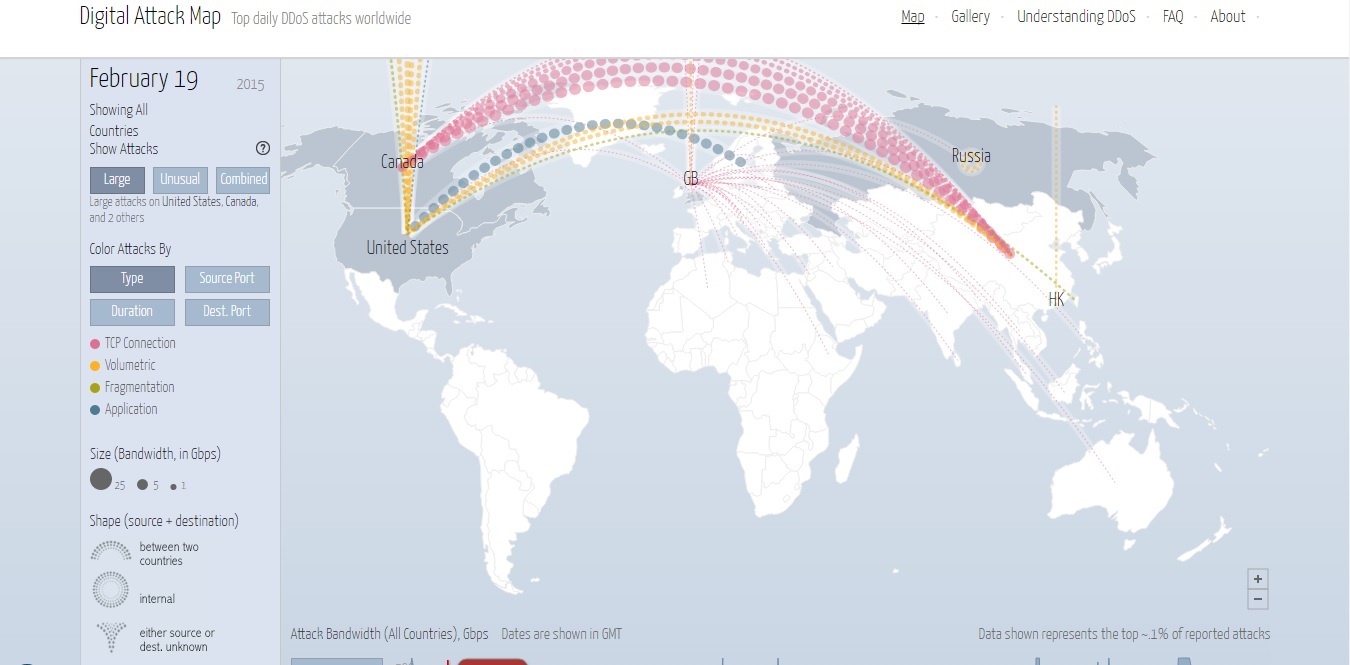
Digital Attack Map - DDoS attacks around the globe. Copy this code into your dismiss. Shows both large and unusual attacks. Attack Bandwidth (), Gbps Dates are shown in GMT Data shown represents the top ~ of reported attacks.
When it comes to real-time cyber attack maps, some are funny, some seem ominous, and all of them tell a story that words alone cannot: cyber attacks never stop. Tamamen yerli ParSecure veri tabanından beslenen canlı siber saldırı haritası. Most of the cyber attack maps online today are just eye candy, but there are some creative ways they can be used.
It’s interesting to watch who is initiating cyber-attack whom globally live. Thousands of website gets hacked every day due to vulnerable files, plugins, misconfiguration on the servers. If your website owner or administrator, you can perform security scan against your website to check vulnerabilities and malware. LIVE CYBER WAR Indonesia Di keroyok. GamerBrain Recommended for you.
ThreatCloud from CheckPoint is another cyber attack map offering a sophisticated way to detect DDoS attacks all over the world. It’s not the most advanced in our list, but it does a good job of showing live stats for today’s and yesterday’s attacks. About Threatbutt Internet Hacking Attack Attribution Map By leveraging our patented Clown Strike technology we are able to harness the raw power of private, hybri public and cumulus cloud system to bring Viking grade threat intelligence to any enterprise. And we made it into a map. Powered by pewpew, even though we made it more accurate because we are a company that does the best threat stuff.
This map shows the geolocation of cyber crime servers that are actively engaged in criminal activity such as credit card theft, credential theft or malware distribution. Every secon the Blueliv Cyber Threat Intelligence Platform collects and analyzes live threat intelligence from hundreds of sources to turn global threat data into predictive. Stronghold Cyber Security is a veteran-owned cyber security company located near historic Gettysburg, Pennsylvania that provides cutting-edge security services to businesses throughout the country. Service offerings include regulatory compliance, penetration testing, advanced cyber risk management, along with customized cyber security programs.
Most embedded malware requires instructions from a command and control server in order to perform pernicious acts such as data exfiltration or scrambling data for ransom. They all seem to show the cyber attacks in a slightly different perspective. This is the Norse attack map as an example: Here is a brief overview of each map : 1. Krebs on Security In-depth security news and investigation. It’s a neat idea, but more of a malware infection map than an attack map, and not terribly.
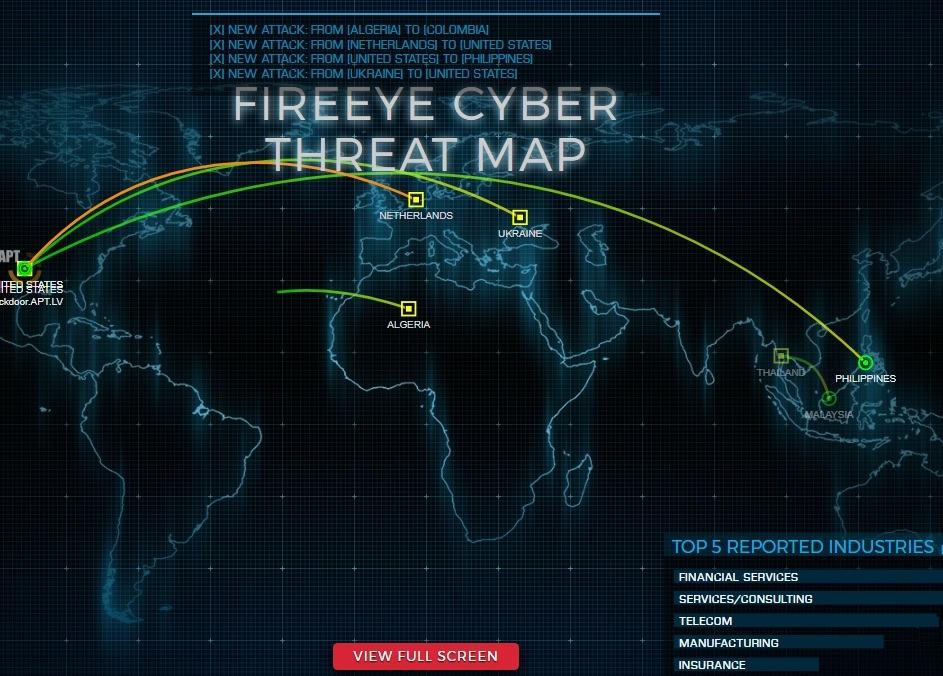
FireEye’s “Cyber Threat Map”. With live hacking and ransomware tracking maps, organizations can now identify hacking attempts or cyber -attacks from different parts of the world as they happen in real time. Real time Hacking Attacks FIRE EYE. Cyberwar Liveuamap - cyber crimes, cyber attacks, informational warfare, desinformation - top technology stories and breaking IT news on live map - cyberwar.
History of Cyberwar conflict. Real-time visibility into global cyber attacks. Did you find it helpful? Press play on the bottom left to see the attacks occur in real-time on the Cyber Attack Map.
View the live attack map showing the off the constant barrage of bot attacks happening right now! Sit back, relax and feel secure with our cyber protection. Check out the top ten cyber attack maps available online and learn how they can help you mitigate cybersecurity threats in a timely manner.
With some maps, you can watch a live feed of attacks happening worldwide. Using these technologies first-hand on the front lines further equips our product teams with a constant source of feedback. View the IP address locations of servers used to control computers infected with malware. More and more security companies use a webpage to show their monitored global security events such as the Live Status of Cyber Attacks being launched from where and who is the target of that attack. It is become interesting by watching those websites.
Actually those are not games but actually happening globally. Kaspersky CYBERTHREAT REAL-TIME MAP 2. The malware WanaCrypt0r 2. What is the Norse Attack Map ?
Hiç yorum yok:
Yorum Gönder
Not: Yalnızca bu blogun üyesi yorum gönderebilir.